
HIPAA-Compliant Cloud Architecture Deep Dive
Introduction
This post is a follow-up to our introductory guide on Designing a HIPAA-Compliant Cloud Architecture for Healthcare Apps on AWS. In this deep dive, we explore the technical layers and implementation details behind building a secure, scalable backend on AWS—specifically tailored for applications that handle Protected Health Information (PHI).
Healthcare startups and innovation-driven providers face a dual challenge: delivering cloud-native performance while meeting the rigorous standards of HIPAA compliance. AWS offers a powerful ecosystem of services to support that goal—but knowing how to assemble those services into a compliant, production-grade architecture requires more than checklists.
This guide is for CTOs, engineers, and digital health founders who want a clear, actionable blueprint for building HIPAA-aligned infrastructure using AWS best practices. We’ll break down key architectural components—Infrastructure as Code, Networking, Compute, Storage, Messaging, Security, Monitoring, Application Layer, Application Security, and DevOps—and explain how to combine them into a resilient, auditable, and compliant platform.
By the end, you’ll understand how to design and deploy a backend that’s ready for scale, ready for audits, and most importantly—ready to protect patient data.
Quick Links
- Introduction
- Architecture Overview
- Infrastructure as Code (IaC)
- Networking and Isolation
- Compute (ECS, Lambda & Serverless Compute)
- Storage (Databases and File Storage)
- Events and Messaging (Decoupling with SQS & SNS)
- Security (Encryption, Identity & Access Management, and Key Management)
- Monitoring, Logging, and Auditing
- Application Layer Considerations (Designing the App for Security)
- Application Security (Authentication, Web Security, and Data Protection in Transit)
- DevOps and Continuous Compliance (CI/CD, Automation, and Governance)
- Conclusion: Achieving Compliance, Security, and Agility on AWS
- Let Us Help You Build a Secure, HIPAA-Compliant AWS Architecture
- Related Insights
Architecture Overview
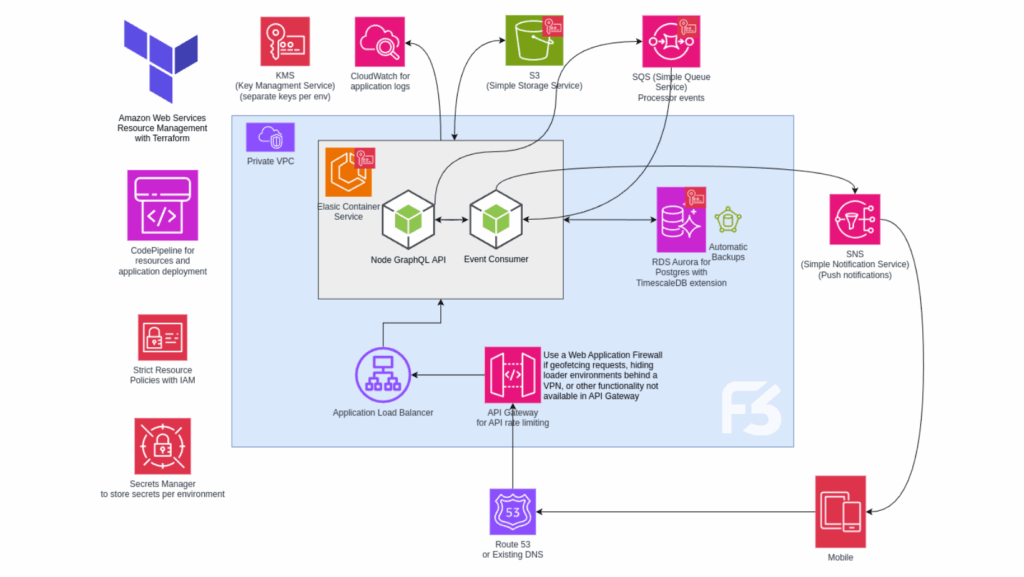
This multi-tier architecture illustrates a secure AWS environment designed for HIPAA-regulated applications. It features isolated VPCs for production and non-production environments, with a public-facing load balancer routing traffic to compute resources in private subnets. Databases and internal services reside in dedicated private subnets, while centralized logging and monitoring (via CloudTrail and CloudWatch) feed into a secured audit account. Core AWS services such as IAM and KMS are integrated throughout to enforce access control and encryption. The design applies a defense-in-depth strategy—ensuring network segmentation, encrypted data handling, real-time visibility, and clear separation of responsibilities across the stack.
Infrastructure as Code (IaC)
Infrastructure as Code: The Foundation of Compliance
A strong foundation for any compliant architecture is Infrastructure as Code, which allows you to define and manage your AWS environment through version-controlled templates.
Consistency and Repeatability with CloudFormation or Terraform
Using AWS CloudFormation or Terraform to script your infrastructure brings consistency and repeatability to deployments. This means every VPC, subnet, database, and server can be created the same way in development, testing, and production, reducing the chance of manual configuration errors.
Built-In Auditability and Secure Deploymen
It also makes your environment auditable: changes to infrastructure are tracked in code commits and CloudFormation change sets, providing a clear history for compliance audits. In fact, AWS provides a Quick Start that uses CloudFormation to deploy a baseline HIPAA architecture, emphasizing repeatable and auditable deployment.
Uniform Security at Scale
Treating your infrastructure as code not only accelerates setup (in minutes, you can launch a full VPC with all required components), but also ensures that security settings (encryption, access policies, etc.) are uniformly applied every time. This approach aligns with HIPAA’s requirement for documented configurations and helps demonstrate that your cloud setup consistently meets required safeguards.
Best Practices for Infrastructure as Code
Best Practices: Store your IaC templates in a source repository and use a CI/CD pipeline (see DevOps section) to deploy changes. Include parameters for environment-specific variables (like key ARNs or subnet IDs) so the same template can spin up separate isolated environments for dev, staging, and production.
This isolation is crucial for HIPAA: for example, you might use completely separate AWS accounts or VPCs for production (with real PHI) versus testing, to prevent any chance of test systems accessing live sensitive. With IaC, such multi-account or multi-VPC setups become easier to manage, and you can enforce that only HIPAA-eligible services are instantiated for PHI processing.
Overall, Infrastructure as Code gives you a controlled, immutable infrastructure where any change is deliberate.
Networking and Isolation
Networking in a HIPAA-compliant AWS architecture revolves around strong isolation and controlled connectivity. At the core is the Amazon Virtual Private Cloud (VPC) – a logically isolated network environment where you can define subnets (segments) to separate different tiers of your application.
Subnet Design and Environment Separation
Best practice is to use private subnets for any components that handle PHI or internal logic (e.g. application servers, databases), and public subnets only for components that must face the internet (e.g. load balancers or a bastion host for admin access). By segregating public-facing and internal resources, you reduce the exposure of sensitive systems. Many organizations even create separate VPCs (or AWS accounts) for each environment – production, staging, development – to further contain any risks and ensure test systems can’t accidentally access production data. If those VPCs need to talk to each other, AWS Transit Gateway can connect them in a hub-and-spoke model, or you can use VPC peering for direct connections.
Traffic Controls and Firewalls
Within each VPC, leverage security groups (virtual firewalls) to restrict traffic at the instance or container level. For example, your database server’s security group should only allow inbound connections from the application server group on the specific database port. Everything else is denied by default. Network ACLs (Access Control Lists) at the subnet level provide an additional layer of filtering for subnet traffic. Also consider AWS Network Firewall or WAF for advanced traffic filtering; AWS Web Application Firewall (WAF), in particular, can protect your web application from common exploits like SQL injection or cross-site scripting at the HTTP level.
Load Balancing and TLS
Load balancing & TLS: Place an Application Load Balancer (ALB) in front of your application cluster. The ALB routes incoming HTTPS requests from clients to your ECS containers or EC2 instances in the private subnets, and it can terminate SSL/TLS at the edge. By offloading TLS to the ALB, you ensure that all public traffic is encrypted via HTTPS (no requests over http are allowed) and you simplify certificate management by using AWS Certificate Manager on the ALB. (Certificate Manager is a service that lets you provision and auto-renew SSL/TLS certificates easily.) HIPAA requires encryption for data in transit, so enforcing TLS 1.2+ for all external connections is a must. Even within your AWS network, you might choose to use TLS for communication between services or use VPC endpoints so that internal traffic to services like S3 or DynamoDB never traverses the public internet – it stays within AWS’s private network For hybrid architectures that connect to on-premises hospital systems or third-party data centers, use AWS Site-to-Site VPN or AWS Direct Connect to create encrypted tunnels for any data exchange, fulfilling transmission security requirements.
Network Monitoring
Finally, implement network monitoring: enable VPC Flow Logs to capture information about IP traffic in your VPC. These logs can be sent to CloudWatch or S3 for analysis and can help detect anomalies or unauthorized access attempts at the network level. In summary, a well-designed network for HIPAA on AWS uses multiple layers of isolation (accounts, VPCs, subnets) and strict traffic controls to ensure that only the necessary data flows occur – and all of them are encrypted and monitored.
Compute (ECS, Lambda & Serverless Compute)
The compute layer of your backend – where your application code and services run – should be designed for both scalability and security. In AWS, you have flexible options for compute, and many of them are HIPAA-eligible under the AWS BAA (Business Associate Agreement). Two popular choices for modern cloud architectures are containerized workloads on Amazon ECS and serverless functions on AWS Lambda. Each offers benefits for a HIPAA-regulated environment:
Amazon Elastic Container Service (ECS)
ECS allows you to run Docker containers in a cluster of EC2 instances or on AWS Fargate (a serverless container runtime). ECS is officially HIPAA-eligible, meaning you can deploy your API and background workers in containers and process PHI, as long as you’ve signed the AWS BAA and configured everything securely. For a HIPAA backend, you would launch ECS tasks in private subnets (no direct internet access) and behind the Application Load Balancer. This ensures that containerized apps (e.g., a Node.js/Express API or a Python Flask app) aren’t exposed directly to the internet. Use Auto Scaling for ECS services to handle usage spikes (for example, many patients hitting the API at once) so that availability – a part of HIPAA’s integrity and availability safeguards – is maintained. With Fargate, AWS manages the underlying EC2 servers, which reduces the ops burden of patching and maintenance (and removes the need to directly handle OS-level HIPAA concerns, since AWS handles the underlying host security). Always keep your container images up to date with security patches and scan them for vulnerabilities (Amazon ECR, the Elastic Container Registry, has built-in image vulnerability scanning). Additionally, assign IAM roles to your ECS tasks (task roles) so that each service has access only to the AWS resources it needs – for example, the image processing service can read/write to a specific S3 bucket and nothing else. This ties into the principle of least privilege at the compute layer.
AWS Lambda
Lambda functions are an excellent way to handle event-driven processing in a HIPAA-compliant way. AWS Lambda is on the list of HIPAA-eligible services, which means you can process PHI within Lambda code (again, provided you’ve signed the BAA). Lambda is great for tasks like processing messages from an SQS queue, resizing images, handling incoming files, or running scheduled jobs, without managing any servers. Because Lambda automatically scales and AWS handles the execution environment, you benefit from built-in high availability and do not have to worry about OS patching – which reduces the risk of missing a critical security update. For HIPAA, treat Lambdas just like any compute: ensure the code is secure (no hard-coded secrets – use AWS Secrets Manager or SSM Parameter Store for any secrets), enable encryption for any data the function might temporarily write (e.g., to /tmp storage or when calling other services), and monitor the execution (Lambda logs go to CloudWatch by default). One thing to note is that Lambda has ephemeral storage and stateless execution by design – this is actually beneficial for compliance, as it means each execution is isolated and data is not persistently stored on the function instances. If your Lambda function processes PHI, make sure that data is encrypted wherever it’s stored afterward (e.g., put results into an encrypted S3 bucket or an RDS database).
ECS And Lambda
In some architectures, you might use a mix of ECS and Lambda. For example, your core API runs on ECS (for fine-grained control over the environment and long-running processes), while certain background tasks or infrequent jobs run as Lambda functions. AWS also offers other compute options like Amazon EKS (managed Kubernetes) or even traditional Amazon EC2 instances. These can be used in a HIPAA-compliant manner too – for instance, EC2 and EKS are HIPAA-eligible – but they come with more management overhead (maintaining servers, patching OS or managing the Kubernetes control plane). If starting fresh, many healthcare startups lean towards ECS/Fargate or Lambda because they minimize the undifferentiated heavy lifting of server management, letting your team focus on application logic. Regardless of the compute choice, ensure that the environments are hardened (only necessary ports open, latest patches, minimal installed packages) and that you maintain runtime security (consider using container security agents or AWS’s security features to detect anomalies in running containers). All admin access to servers or containers should be via secure methods (SSH over VPN or Session Manager, with MFA for admins). With these compute services properly configured, your application layer can safely process sensitive health data at scale.
Storage (Databases and File Storage)
Healthcare applications deal with various types of data – from patient records in databases to medical images and documents stored as files. AWS provides HIPAA-eligible storage services that cover both structured and unstructured data, with robust security features to protect PHI.
Amazon RDS (Relational Database Service)
For structured data (like patient info, EHR data, transaction logs), Amazon RDS is a managed database service that supports engines like PostgreSQL, MySQL, and others. AWS RDS (including Amazon Aurora) is HIPAA-eligible and ideal for storing ePHI in a controlled way. You should enable encryption at rest for your RDS databases from the start – this is as simple as a checkbox (or parameter in CloudFormation) to have the database files encrypted with AWS KMS keys.
Encryption ensures that even if someone were to somehow get ahold of a disk snapshot, the data is unreadable without the key. Use AWS Key Management Service (KMS) to manage those encryption keys (we’ll talk more about KMS in Security below). RDS also supports TLS/SSL connections, so require your application to connect to the database using TLS to encrypt data in transit as well.
Beyond encryption, RDS offers features that help with availability and disaster recovery, which are important for HIPAA’s continuity planning: you can deploy your database in a Multi-AZ configuration, meaning RDS will keep a synchronous standby in a second Availability Zone. If the primary fails, it fails over to the standby automatically, improving resilience.
Enable automated backups on RDS with a retention period that meets your organizational policies (and potentially regulatory expectations – many keep at least daily backups for 30 days or more)flatirons.com. RDS backups are also stored in encrypted form.
You might also create read replicas for offloading analytics or reporting queries – this way, primary database performance isn’t impacted by heavy reads, and you can tightly control who has access to PHI on the primary versus a replica (e.g., give data analysts access only to a replica with de-identified data)flatirons.com.
Additionally, consider using Database Activity Streams or enabling detailed logs (e.g., PostgreSQL’s query logging) to capture access to sensitive tables – these logs can be forwarded to CloudWatch for monitoring unusual queries as part of your audit program.
Amazon S3 (Simple Storage Service)
S3 is AWS’s scalable object storage, perfect for storing unstructured data such as medical images (X-rays, MRIs), documents, or even backups and log files. Amazon S3 is HIPAA-eligible and widely used for PHI storage due to its fine-grained security controls.
First and foremost, secure your buckets: never store PHI in an S3 bucket that is open to the public. Utilize S3’s Block Public Access settings to ensure no public exposure occurs by accident.
Like RDS, S3 can (and should) be configured to encrypt data at rest automatically. You can use S3 Server-Side Encryption with KMS (SSE-KMS) so that each object is encrypted with a KMS key you controljustaftermidnight247.com. This gives you an audit trail on key usage and the ability to revoke access if needed.
For an extra layer, some choose to implement client-side encryption as well (encrypt data before uploading to S3), but for most cases SSE-KMS suffices when properly managed.
When your application needs to serve files (e.g., a user downloading their lab report PDF), do not make the bucket public; instead, have your backend generate pre-signed URLs or use Amazon CloudFront with signed URLs for content delivery. A pre-signed URL is a temporary link that grants time-limited access to a specific object – this way, even authenticated users only get to the specific file they’re allowed to, and only for a short window of time.
This approach was highlighted as a best practice: restrict S3 bucket access to only the app, and expose expiring URLs to clients as neededflatirons.com. It ensures that the raw S3 locations and objects remain hidden and secure.
Data Archival and Backup Storage
In healthcare, retention of records for many years might be necessary. Amazon S3 integrates with Glacier storage classes (Glacier Instant Retrieval, Glacier Flexible, Glacier Deep Archive) which are suitable for long-term archival of infrequently accessed data at lower cost.
You can set lifecycle rules on S3 buckets to move older objects (say, after a year) into Glacier Deep Archive for cost savings, while still maintaining them in a secure, encrypted state for, say, the 6 or 7 years you need to keep them.
For database backups, you can copy RDS snapshots to another region or export them to S3 (which can then transition to Glacier) for an added disaster recovery measure (off-site backup).
AWS also offers AWS Backup, a service that can manage and automate backups across RDS, EBS, DynamoDB, etc., from a central placeexabeam.com. This service can ensure backups are taken on schedule and retained according to your defined policies – useful for meeting the HIPAA requirement of having a robust disaster recovery and backup plan.
All storage should be accompanied by proper access control (IAM policies, S3 bucket policies, etc.) to ensure only the right identities or services can read or write the data. We will discuss identity and access in the Security section, but remember that storage security is a combination of encryption and access rules. Also, monitor your storage: enable S3 Access Logs or CloudTrail data events for S3 to log any access to sensitive buckets (so you can see if someone, even an internal account, accesses data they shouldn’t). By using AWS’s managed storage services with these security features, you significantly reduce the risk of a data breach of PHI and create a clear audit trail of how data is stored and used.
Access Control and Monitoring
All storage should be accompanied by proper access control (IAM policies, S3 bucket policies, etc.) to ensure only the right identities or services can read or write the data.
We will discuss identity and access in the Security section, but remember that storage security is a combination of encryption and access rules.
Also, monitor your storage: enable S3 Access Logs or CloudTrail data events for S3 to log any access to sensitive buckets (so you can see if someone, even an internal account, accesses data they shouldn’t).
By using AWS’s managed storage services with these security features, you significantly reduce the risk of data breaches, ensure visibility into access patterns, and create a clear audit trail—essential components for maintaining HIPAA compliance in any healthcare application.
Events and Messaging (Decoupling with SQS & SNS)
In a complex healthcare application, different components often need to communicate or pass data asynchronously – for example, an event when a lab result is ready, or a background job to send a notification. AWS offers messaging services like Amazon SQS and Amazon SNS that help decouple these components and improve resilience and scalability. Importantly, these services are also HIPAA-eligible, meaning they can be used to transmit or handle PHI within a covered environment (with the usual caveat: you must still ensure the messages themselves are protected).
Amazon SQS (Simple Queue Service)
SQS is a message queuing service that lets you send, store, and receive messages between software components, without losing messages if one part is slower or temporarily unavailable. In a HIPAA context, SQS is great for buffering workload. For instance, when a user uploads a large medical image that needs processing, your front-end service can put a message into an SQS queue describing the task (with a reference to the image in S3). A separate worker (maybe a Lambda function or an ECS service) can then pull from the queue and perform the processing asynchronously. This improves user response time and decouples the front end from the heavy lifting.
To keep SQS compliant: enable SQS SSE (Server-Side Encryption) so that all messages are encrypted at rest in the queue with a KMS key. This ensures any PHI in the message content is encrypted on the disk. Also, control access to the queue via IAM policies – only your producer and consumer services should have rights to send or receive from the queue.
If using AWS Fargate/ECS tasks to process messages, you can deploy the SQS consumer tasks in the same VPC (with no public access) and use a VPC Endpoint for SQS, which forces all queue operations to remain within AWS’s private network. This way, even the act of polling the queue doesn’t traverse the internet.
SQS provides excellent reliability (messages are redundantly stored across multiple AZs) and can scale to handle high throughput, ensuring that spiky workloads (say, a thousand appointment reminders to send at once) don’t overwhelm any single component – they’ll just queue up and be processed in turn.
Amazon SNS (Simple Notification Service)
SNS is a pub/sub messaging service, often used for sending out notifications to multiple subscribers. In healthcare apps, SNS can serve various purposes. One common use is to send mobile push notifications or SMS messages to patients (for appointment reminders, prescription ready alerts, etc.) by integrating SNS with mobile push services or SMS.
Another use is internal: SNS can fan-out events to various systems – for example, when a new patient record is created, SNS could notify other microservices that might need to act (one to send a welcome email, another to update analytics, etc.).
Like SQS, SNS supports encryption at rest using KMS-managed keys, so enable that on any topic that might handle sensitive data. Also, SNS allows message filtering and attributes, which can help route messages appropriately to different subscribers without exposing unnecessary data.
For push notifications or SMS that involve PHI, be very careful: ideally avoid putting actual PHI in the notification text (HIPAA has rules about communications; a generic “You have a new message in the portal” is safer than an SMS that contains medical details). Use SNS primarily to notify or wake up systems or users, and let them securely fetch the actual data from the app if needed (under authentication).
AWS SNS, being fully managed, handles the heavy lifting of delivery and retries, and you can integrate it with AWS Lambda or SQS (for example, have SNS topic deliver to an SQS queue or Lambda for further processing).
For HIPAA workloads, an example pattern is: an SNS topic for “New Lab Result” events might have two subscribers – one is a Lambda that will format and send a secure message to the patient (e.g., via email/SMS through a secure channel), and another subscriber might be an audit logging service that simply logs that a result was released. All of these can be done without exposing PHI in transit.
As with SQS, restrict who/what can publish to or subscribe from your SNS topics using IAM and SNS access policies.
Resilience, Availability, and Security Considerations
By leveraging SQS and SNS, you build a more fault-tolerant architecture – components can go offline or scale independently – which aligns with HIPAA’s focus on availability and robust contingency planning.
In case one service goes down, the messages persist in a queue and can be processed later, rather than being lost. Just ensure the messaging layer itself is secured (encryption and access control) because if someone maliciously gained access to your queue or topic, they could potentially read or inject sensitive messages.
With AWS providing encryption and access features, the onus is on you to configure them correctly. When done right, SQS and SNS become powerful tools in a HIPAA-compliant architecture for handling asynchronous workflows, notifications, and system decoupling.
Security (Encryption, Identity & Access Management, and Key Management)
Security is at the heart of HIPAA compliance. AWS operates on a shared responsibility model for security: AWS manages the security of the cloud (physical data centers, infrastructure, and ensuring their services can be used securely), while you are responsible for security in the cloud (configuring services correctly, managing user access, and protecting data). In this section, we focus on the cloud security measures you should implement – notably encryption and access controls – using AWS’s security services.
Encryption and Key Management: Protecting ePHI via encryption is a common HIPAA safeguard to ensure data confidentiality. AWS makes it straightforward to encrypt data at rest and in transit, but it’s up to you to use those features. We’ve already mentioned enabling encryption for RDS and S3, but a critical component behind the scenes is AWS Key Management Service (KMS). KMS is a secure key management service that lets you create and control cryptographic keys. When you enable “encryption” on an S3 bucket or RDS, AWS will use KMS keys (or an AWS-managed key by default) to do the encryption. For HIPAA compliance, it’s recommended to use customer-managed KMS keys so that you have full control: you can set rotation policies (for example, auto-rotate the key annually), define usage permissions, and even disable or revoke keys if needed. Each environment (dev, prod) can have its own set of keys to ensure separation. KMS keys themselves should be secured – limit who in your team can administer or use them. KMS integrates with CloudTrail, so every use of a key (for decryption or encryption) is logged, giving you an audit trail of key usage. A good practice is to enforce that only specific IAM roles (like an EC2 role or Lambda role) are allowed to use a particular KMS key to decrypt data; this ties the ability to decrypt PHI to the identity of the service that truly needs it. Besides storage encryption, use KMS for other secrets or sensitive data: for instance, if you need to store sensitive configuration values, use AWS Secrets Manager or SSM Parameter Store (SecureString parameters), which both rely on KMS to encrypt secrets. This way, database passwords, API keys, or private certificates are not stored in plaintext anywhere.
For encryption in transit, AWS Certificate Manager (ACM) was mentioned as a tool to manage SSL/TLS certificates. ACM can provision certificates for your domain and manage their renewal, which you then attach to your ALB or CloudFront distributions for HTTPS. Enforce TLS everywhere: clients should interact with your application only over HTTPS, and your internal services should use encrypted channels or stay within a private network. As per the latest guidelines, using TLS 1.2 or higher is required (TLS 1.3 is recommended when possible). This ensures strong encryption for data in transit, meeting HIPAA’s transmission security rules. For internal service-to-service calls (like an ECS service calling another ECS service), consider using private VPC endpoints or at least ensure that if you use hostnames, they resolve to internal IPs and traffic doesn’t leave AWS network. Optionally, you can issue internal TLS certificates (through ACM Private CA or even self-signed certs distributed to your services) if you want to encrypt traffic between microservices, though many rely on network isolation instead.
Identity and Access Management (IAM): AWS IAM is the control center for access in AWS. With IAM, you create users, groups, and roles and attach policies that define what actions are allowed or denied. HIPAA’s Security Rule puts heavy emphasis on access control – only authorized individuals or processes should access PHI, and they should have the minimum necessary access (“least privilege”). IAM enables this by allowing you to craft fine-grained policies. For example, you can create an IAM policy that allows a specific EC2 instance (or ECS task role) to read from a particular S3 bucket and nothing else. Or a policy that allows your data analyst role to query a read-replica database but not modify anything. Regularly review IAM policies and remove any excessive permissions. Use IAM Roles for services rather than static access keys whenever possible – roles provide temporary credentials and can be constrained to specific resources, whereas access keys can be leaked or misused if not rotated. For human access (like developers or admins using AWS), set up IAM users (or use AWS SSO with an identity provider for better control) and always require Multi-Factor Authentication (MFA) for privileged accounts. In fact, by 2024, MFA is essentially considered mandatory for administrative access in any serious security framework, and is highly advised (if not explicitly required) by HIPAA guidance for any access to sensitive systems. AWS supports virtual MFA apps or hardware keys for IAM users – enforce MFA in the IAM policy (you can have a condition that the user must be MFA-authenticated). You should also consider enforcing password policies for IAM users (if any) that align with best practices – e.g., minimum length, complexity, and rotation periods as appropriate.
For application-level user management (the end-users of your application, like patients, doctors, etc.), AWS Cognito is a great service that is HIPAA-eligible and can manage sign-ups, sign-ins, and user profiles securely. Amazon Cognito User Pools store user credentials (with password hashing, etc.) and can enforce strong password requirements and even MFA for your application’s users. For example, you can require that patients use MFA to access especially sensitive data, which adds an extra layer of protection in case credentials are stolen. Cognito can also integrate with external identity providers (like Google, Apple, or enterprise SAML providers for hospital staff single sign-on), but all in a way that offloads the heavy lifting of authentication from your app code. Using Cognito means you as a developer don’t need to handle passwords (which is a liability) – Cognito will handle password resets, account verification, and token generation. It supports industry standards like OAUTH2 and OIDC, so you can secure your API by validating Cognito-issued JWT tokens on each request, ensuring that only authenticated users with valid tokens can hit protected endpoints. This satisfies the HIPAA requirement for unique user identification and authentication in a robust way (each user has their Cognito identity, and you can get audit logs of logins, etc.). In short, IAM secures access between components and AWS resources, while Cognito secures access for end-users of the application – together, they cover the spectrum of access control.
Principle of Least Privilege & Monitoring: Implement the principle of least privilege everywhere – only give each user or service the minimal access required. For instance, if a Lambda function only needs to put messages to an SNS topic, its IAM role should not have access to anything else (no S3, no DynamoDB, etc., unless needed). This minimizes the impact if that function is exploited – the blast radius is small. Use IAM resource-level permissions where possible (like permitting access to only arn:aws:s3:::my-app-bucket/uploads/* rather than all of my-app-bucket). AWS IAM Access Analyzer is a tool that can help find overly-broad access (for example, it can alert you if a policy allows some access from * or if an S3 bucket is unintentionally public). This is very useful for a compliance audit perspective – you can demonstrate that you have checks in place for misconfigurations. Moreover, you can use AWS Config rules or AWS Security Hub to continuously evaluate your IAM setup against best practices. Security Hub has a set of foundational security best practice controls and can alert if, say, an IAM user has not enabled MFA or if access keys are not rotated. (Security Hub doesn’t yet have a specific “HIPAA” standard out of the box, but many of its checks align with common compliance needs.)
Secrets Management: Do not store sensitive credentials in code or in plaintext on disk. Use AWS Secrets Manager to store things like database credentials, API keys for third-party services, etc. Secrets Manager will keep them encrypted (using KMS) and allows you to set up rotation (for example, it can automatically rotate an RDS password every 90 days by creating a new one and updating the DB). Your application can retrieve secrets at runtime through a secure API call to Secrets Manager (which requires it to have the right IAM permission). This ensures that even if someone scans your code repository or configuration, they won’t find hard-coded secrets. It also provides an audit trail for secret usage and rotation.
Summary of Security Controls: Below is a quick summary table of how key HIPAA security safeguards map to AWS features in this architecture:
| HIPAA Safeguard | AWS Implementation | Example in Architecture |
|---|---|---|
| Encryption (Data at rest & in transit) | – AWS KMS for managing encryption keys – Built-in encryption for data stores (enable SSE-KMS on S3 buckets, RDS, EBS volumes, etc.) – AWS Certificate Manager (ACM) for TLS certificates | Encrypt all PHI at rest using KMS keys (e.g., S3 objects, database storage). Enforce TLS 1.2+ for data in transit using ACM-issued certificates on load balancers. |
| Access Control (Least privilege & authentication) | – AWS IAM for fine-grained access policies and roles – Amazon Cognito for application user identity management (with MFA support) – IAM multi-factor authentication for AWS administrators | Use IAM roles to ensure each microservice or component can only access the resources it need. Manage end-user logins via Cognito (HIPAA eligible) with mandatory MFA for admin users and optional MFA for end-users for sensitive actions. |
| Audit Logging (Monitoring of access and changes) | – AWS CloudTrail for API activity logging – AWS CloudWatch for operational logs and metrics – AWS Config and AWS Security Hub for configuration auditing and alerts | Enable CloudTrail across all AWS accounts to log every API call (e.g., access to S3 objects, IAM changes) and retain these logs for at least 6 years for complianc. Use CloudWatch Logs for application logs (with PHI masked) and set up alerts (via SNS) for suspicious events (e.g., multiple failed logins). AWS Config can flag if any resource drifts from security baseline (e.g., an S3 bucket becomes public). |
| Disaster Recovery (Availability & backups) | – Multi-AZ deployments for critical systems (RDS, ECS services spread across AZs) – Automated backups and snapshots (RDS automated backups, EBS snapshots, AWS Backup service) – Redundancy and failover (standby instances, cross-region replication for data) | Deploy databases and caches in Multi-AZ mode so they continue operating if an AZ fails. Schedule daily backups of databases with RDS (and use AWS Backup for centralized backup management). Replicate backed-up data (or use read replicas) in a second region to ensure recoverability even if an entire region has an outage. Periodically test your disaster recovery by restoring backups to verify data integrity. |
By implementing the above security measures, you establish defense in depth – even if one layer is breached, others still protect the data. For example, if an attacker compromised an application server, they would still face encrypted data (needing KMS keys) and tightly scoped IAM roles that prevent pivoting to other resources. And you would have logs to detect and analyze the incident. Always remember: security in AWS is continuous. Make use of AWS’s native tools to automate checks (e.g., AWS GuardDuty for threat detection, Amazon Macie for scanning S3 buckets for sensitive data exposure) so that if something does slip, you catch it quickly. In fact, Amazon Macie is a managed service that uses machine learning to discover and classify sensitive data (including PHI) in S3, which can be a boon for ensuring you haven’t inadvertently stored PHI in an unsanctioned location. It integrates with Security Hub and EventBridge to alert you if, say, a bucket contains files with patient identifiers that should not be there. Utilizing such tools helps maintain continuous compliance over time, rather than just a point-in-time adherence.
Monitoring, Logging, and Auditing
Continuous monitoring and auditing are what turn a secure architecture into a compliant one. Under HIPAA, you must be able to record and examine activity in systems handling PHI – this is crucial for detecting unauthorized access or modifications. AWS provides a suite of monitoring services that, when configured properly, give you deep visibility into your environment.
Amazon CloudWatch (Metrics, Logs, Alarms): CloudWatch is the central service for monitoring AWS resources and your own applications. It collects metrics from services (CPU utilization of EC2 instances, memory of containers, latency of load balancer requests, etc.) and can also ingest custom metrics. For a healthcare app, you might watch metrics like number of login attempts, error rates on APIs, or queue lengths (which might indicate a processing backlog). CloudWatch Logs is particularly useful for aggregating application logs, system logs, and custom audit logs. Ensure that all your application components (ECS tasks, Lambda functions, etc.) send their logs to CloudWatch or another centralized log system. For example, ECS tasks (with AWS Logs driver) and Lambda will by default pipe stdout logs to CloudWatch Logs. These logs can include important audit information like user ID accessing a resource, or an error stack trace that might indicate a security issue. However, be cautious not to log PHI in plaintext – you should mask or avoid sensitive fields in logs to prevent creating another surface where PHI resides.
Set up CloudWatch Alarms on key metrics and events. For instance, alarm on high error rates, or on suspicious patterns like a sudden spike in outbound network traffic (could indicate data exfiltration). If an alarm triggers, CloudWatch can notify the team via Amazon SNS (send an email/SMS or trigger a Lambda for automated response). As an example, you could have an alarm for “5 failed login attempts for the same user within 1 minute” which then sends an SNS notification to the security officer or locks the user account temporarily – this could indicate a brute force attempt. Another example: an alarm if an EC2 instance’s CPU goes to near 100% unexpectedly, which might suggest a rogue process (possibly a breach, or just a heavy workload – either way merits investigation).
AWS CloudTrail (User Activity Tracking): CloudTrail is often described as the CCTV of your AWS account – it records every single API call that happens in your AWS environment, whether by a user, an application using credentials, or by AWS services on your behalf. For HIPAA, CloudTrail is indispensable for audit logs. It will log events like: IAM user John deleted an S3 object at 3:45 PM, or an ECS task accessed the KMS key to decrypt something, or someone changed a security group rule. These events go into log files that you can direct to an S3 bucket (which of course should be encrypted and access-controlled). CloudTrail logs should be enabled on all accounts, and consider turning on CloudTrail Insights for detection of unusual API activity (it can spot anomalies like a burst of delete operations, etc.). The presence of CloudTrail is “almost designed for things like HIPAA compliance” since it provides a record for auditing and incident investigation. Many compliance assessments will ask: do you have audit logs of access to PHI and modifications? With CloudTrail, you can confidently say yes. It’s important to protect CloudTrail logs – use a dedicated S3 bucket just for logs, with strict permissions (perhaps even keep it in a separate audit account). Enable CloudTrail log file validation which creates a hash to ensure logs haven’t been tampered with. You may also integrate CloudTrail with a SIEM (Security Information and Event Management) system or AWS’s own services like Amazon CloudWatch or AWS Security Hub to generate alerts on certain events (e.g., creation of an IAM user, disabling of a KMS key, etc., could all be notable events in a HIPAA environment).
AWS Config & Security Hub: AWS Config is a service that continuously checks the configuration of your resources against rules. For example, you can have a rule that “S3 buckets must have versioning enabled and public access blocked” or “RDS instances must be encrypted”. If a resource drifts from these rules, Config flags it. This is useful for catching misconfigurations in real-time before they become incidents. You can even have Config rules automatically remediate issues (like auto-enable encryption if someone created a bucket without it, though in many cases you’d prevent that creation in the first place). For compliance, AWS Config provides a history of configuration changes – so you can answer “who changed this security group and what was it before?”. AWS Security Hub is a dashboard that can aggregate findings from Config, GuardDuty, Macie, and more. It comes with security standards checks, including AWS’s foundational best practices. While not HIPAA-specific, it covers a lot of ground (like ensuring MFA enabled, no public S3, etc., many of which line up with HIPAA requirements). Security Hub can show your overall compliance score and list out failed controls. For example, it would flag if any EC2 instance is not logging to CloudWatch or if any IAM user has console access without MFA – things directly related to safeguarding data. Treat Security Hub findings seriously: each finding is an opportunity to tighten security. You can even set up automatic ticketing or notifications for any high-severity findings.
Application Monitoring: Beyond infrastructure, monitor the application itself. Implement application-level logging for significant events: e.g., user login success/failure, records viewed or edited (at least by admin users), and any use of elevated privileges in the app. This is more about the application audit trail, which a HIPAA-covered app should have (so that you can later say, “this patient record was viewed by Dr. X on this date”). Some of this may be handled in the app or via the database logs. But ensure those logs are stored securely and are immutable (or at least versioned) to prevent tampering – writing them to append-only storage like CloudWatch Logs or an external system helps.
Additionally, consider Amazon CloudWatch ServiceLens or X-Ray for tracing if you have a microservices architecture. These can help detect performance issues or errors in complex request flows (for example, an API call that goes through several services). While that’s more performance than security, a slow-down or error could be a sign of something like an attack (e.g., someone fuzzing your API with bad requests). Setting up synthetic monitors (CloudWatch Synthetics) to check your API endpoints regularly can also ensure you catch downtime or anomalous responses quickly – which feeds into availability monitoring.
Incident Response and Alerts: Define clear procedures for responding to security alerts or incidents. AWS has tools to help, but your team should know what to do when an alarm goes off. For instance, if CloudTrail shows an unauthorized API call or CloudWatch alarm flags high error rate indicating possible abuse, have runbooks: perhaps automatically quarantine an instance (you could use AWS Systems Manager to execute a runbook), rotate credentials, or engage your security team. Using AWS SNS or EventBridge, you can wire up automated responses to certain triggers – e.g., if an IAM policy is made more permissive, automatically revert the change or at least notify immediately. This kind of automation and preparedness is part of what auditors look for in demonstrating that you can identify and respond to incidents (a requirement in HIPAA’s security rule).
Finally, ensure that all these logs and monitoring data are retained for an appropriate period. While HIPAA doesn’t mandate a specific retention for logs, a common practice is to retain audit logs for at least 6 years (since HIPAA requires documentation and records of disclosures to be kept for 6 years). CloudTrail logs in S3 can have a lifecycle policy to archive to Glacier after a few months and delete after 7 years, for example. CloudWatch Logs can be set with retention policies (e.g., retain 1 year, or export to S3 for longer storage if needed).
In summary, monitoring and auditing on AWS should be multi-layered: infrastructure-level (CloudTrail, Config), service-level (CloudWatch metrics/logs), and application-level (app logs, user activity). Combined, these give you the visibility to detect anomalies, investigate incidents, and provide evidence of compliance. As one source puts it, detecting unauthorized access and maintaining logs are essential for HIPAA-compliant apps, and services like CloudTrail are built with this in mind. By proactively watching your environment, you can catch potential issues early and document every action in case you need to demonstrate compliance or investigate a breach.
Application Layer Considerations (Designing the App for Security)
The application layer is the code and business logic of your healthcare application – typically the API servers, background jobs, etc., that you develop. While the focus of this article is cloud architecture, it’s worth highlighting some best practices at the application layer that complement the secure AWS infrastructure.
Tech Stack & Framework: You have freedom in choosing your tech stack on AWS, but ensure whatever you choose is actively maintained and supports modern security practices. Common choices include Node.js with Express or a Python framework like Django/Flask, Java Spring Boot, or .NET Core – all of which can run smoothly on ECS or Lambda. The example architecture we outlined could, for instance, use Node.js (LTS) and Express.js for a RESTful or GraphQL API, with TypeScript to catch type errors and improve code quality. In fact, using GraphQL could allow clients to request just the data they need, which can be efficient, but be sure to implement query depth limits to prevent abuse. Regardless of language, use frameworks that have good security track records and support features like input validation, output encoding, and protection against common vulnerabilities. Express has middleware for security (like Helmet for setting HTTP headers), and frameworks like Django have built-in protections for SQL injection, XSS, CSRF, etc. Leverage these.
Secure Coding Practices: Train your development team on OWASP Top 10 vulnerabilities and how to avoid them. For example, when interacting with the database, always use parameterized queries or an ORM to prevent SQL injection. Validate and sanitize all inputs (never trust client data – enforce length, type, and format where possible). This is especially critical in healthcare apps where an injection flaw could potentially expose a large amount of patient data. Implement proper error handling so that internal errors don’t leak information (e.g., stack traces) to users. Logging is important, but avoid logging sensitive data. If you must log an identifier, consider using an internal patient ID that’s not a real SSN or anything sensitive.
Data Minimization and Tokenization: Only collect and store the minimum PHI that you need for your application’s purpose – this is a principle of HIPAA as well as general privacy law. If possible, tokenize or pseudonymize data. For example, if you need to use real patient data in a lower environment for testing (generally avoid if you can), ensure it’s de-identified. Within the production environment, consider extra encryption at the application level for particularly sensitive fields (e.g., encrypting a column in the database using a key that the application holds via KMS). This would mean even if the DB is compromised, the most sensitive data is not immediately readable. Some apps implement field-level encryption or use services like AWS CloudHSM or custom encryption libraries for this purpose.
Integrations and APIs: Many health apps integrate with third-party services (for example, electronic health record systems, billing providers, etc.). Use secure APIs and ensure any third-party also signs a BAA if they handle PHI. When your app calls external APIs, do so over HTTPS and authenticate appropriately (never include secrets in the URL, use headers or other secure methods). If integrating with AWS services (like calling AWS S3 or SQS from your code), use the official AWS SDKs which handle secure authentication (SIGv4 signing) for you. For instance, using the AWS SDK for JavaScript (in Node) or boto3 in Python will automatically use the IAM role credentials in the environment, so you don’t need to hardcode keys.
Performance & Scalability: A well-architected app ensures good performance, which indirectly plays into security (e.g., an overloaded system might drop security checks or fail open). Utilize AWS auto-scaling, but also design your algorithms to scale. Use caching where appropriate (maybe an in-memory cache or Amazon ElastiCache – which is also HIPAA-eligible – for frequently accessed data) to reduce load on databases. Just ensure your cache is configured not to accidentally serve one user’s data to another (cache keys should include user context if caching user-specific data). For file processing or large data, consider streaming data instead of loading huge blobs in memory, to avoid performance bottlenecks that could cause system crashes.
Testing and QA: Incorporate security testing in your development lifecycle. This can include static code analysis (tools that scan your code for potential vulnerabilities), dependency scanning (checking your open-source libraries for known vulnerabilities – AWS CodeGuru or third-party tools can help with that), and dynamic testing. Before going live, or regularly, consider penetration testing your application. AWS allows you to pen-test your own AWS-hosted applications (with some guidelines – e.g., no DNS brute forcing of AWS infrastructure). This can find issues like misconfigured permissions or application logic flaws. Also, run drills for incident response at the application level – e.g., what if an API key is leaked, can you rotate it quickly (AWS Secrets Manager can help here if used)? What if a patient somehow accesses another patient’s data due to a bug – do you have monitoring to catch that?
Workflow and Data Integrity: Ensure that your application enforces roles and scopes properly. For example, a doctor should only see their patients, and a patient should only see their own data. Use proven patterns for multi-tenant data isolation if your app serves multiple clinics or organizations. AWS Cognito can help by providing user groups or app client scopes, but much of this must be coded in your application logic too (like including the user’s tenant ID in every query to restrict results). Integrity is another aspect of HIPAA – you need to protect data from improper alteration. Database constraints, transactions, and even features like AWS Database Migration Service for ongoing replication to a backup can help ensure data isn’t lost or corrupted.
In summary, the application layer should be built with a “security-first” mindset to complement the AWS infrastructure security. The most hardened cloud setup can be undermined by an application bug or negligence (like leaving an admin backdoor open or storing passwords in plaintext). Conversely, a secure application running on a secure cloud infrastructure yields a strong overall solution. Document your application’s security features and logic for auditing purposes – sometimes, auditors will want to know things like how you ensure a user can only access their records. You can then point to your role-based access control in the app, backed by Cognito and IAM, etc., as evidence. Keeping application security in focus from the design phase will save a lot of headache down the road and ensure that your app truly keeps patient data safe.
Application Security (Authentication, Web Security, and Data Protection in Transit)
While we touched on some security aspects in the app layer, let’s explicitly address application security features that every healthcare app should have when running in the cloud. These are the safeguards that users and clients of your application directly interact with – authentication, authorization, and secure communication.
User Authentication & Authorization: One of the easiest ways to implement a secure user auth system on AWS is by using Amazon Cognito User Pools. As noted, Cognito is HIPAA-eligible and provides a fully managed user directory with support for features like Multi-Factor Authentication (MFA), password policies, and account recovery. Enabling MFA (using SMS or authenticator apps) for user logins can significantly improve security – in fact, regulatory guidance by 2024 has effectively moved MFA from “highly recommended” to “expected” for systems dealing with sensitive data. You might require it for all users, or at least for privileged users (like admin portals for clinicians). Cognito can enforce MFA and even adaptive authentication checks. It also supports sending logs to CloudWatch for login events, so you get an audit trail of user access. If Cognito doesn’t fit your scenario (say you have an existing identity provider), AWS supports integration via AWS IAM Identity Center (AWS SSO) or federation protocols. The key is: implement a robust identity layer where each user has a unique account, and never share accounts. Assign roles or groups to users to limit what data they can see – for example, user John Doe (a patient) should only be able to access resources he owns, while Dr. Smith (a provider) can access records of patients under her care. This authorization logic can be enforced both in the application code and by using token claims (for instance, a Cognito JWT might include user roles or tenant info that your API can check). For fine-grained permissions within your app (like limiting specific actions), AWS has a newer service called Amazon Verified Permissions (which is now HIPAA eligible) that can work with Cognito to handle authorization decisions, though you could also implement simpler role-check logic directly.
End-to-End Encryption (TLS Everywhere): We’ve stressed encryption in transit, but it bears repeating at the application level: all client-app communication must be over HTTPS. Your domain for the API should have an SSL certificate (via ACM or other CA) and the TLS configuration should prefer modern ciphers. On AWS, if you use an ALB or CloudFront, you can choose a security policy (e.g., ELBSecurityPolicy-TLS13-1-2-2021-06) that ensures only TLS1.2 and 1.3 are allowed. The ALB will handle the encryption with clients. If your application is a web app or mobile app that talks to the backend, make sure it only ever uses https:// endpoints. This not only protects data from eavesdropping, but also guards against modification in transit. For internal services (e.g., a call from your API service to a microservice), keep those calls within the VPC or also encrypted. AWS’s network is already quite secure, but internal TLS can add protection if you have to traverse multiple VPCs or go over the internet (in the case of cross-region calls if not using AWS’s private backbone).
Web Application Firewall (WAF): AWS WAF is a service you can use with ALB, API Gateway, or CloudFront to filter incoming traffic based on rules. It’s worth considering adding a WAF in front of your application to mitigate web exploits at the edge. AWS WAF comes with managed rule sets, including ones for common vulnerabilities (SQLi, XSS), known bad IP addresses, bots, etc. For a healthcare app, you might enable the Core rule set and maybe specific ones like “SQL database injection” rule set. This is not a substitute for secure code, but a defense in case something slips. WAF can also rate-limit clients – for example, to block basic denial-of-service or brute force attempts (if someone tries 1000 login attempts, WAF can block that IP). Since patient data is high-value, health apps could be targets of attack, and WAF provides an additional gate. Notably, AWS Shield Standard is automatically applied (free) to protect against DDoS at the network layer, but WAF is needed for application layer attacks.
CORS and API Security: If your backend is consumed by a web front end from a different origin (e.g., a JavaScript front-end hosted elsewhere or a mobile app making calls), configure Cross-Origin Resource Sharing (CORS) rules properly on your API. This isn’t a HIPAA issue per se, but it’s a common security setup to prevent unwanted scripts from other sites from calling your API. Restrict allowed origins to your known frontend domain(s), and use secure headers. Similarly, use secure cookies (HTTPOnly, Secure, SameSite attributes) if your web app uses cookies for session; or if using JWT tokens in a SPA, consider storage mechanisms carefully (tokens in memory or cookie, to avoid XSS leaks).
Data Integrity and Validation: At the app level, implement checksums or versioning for important data if needed. For example, if you’re transmitting lab results from a device to the cloud, using a hash to verify the data didn’t change in transit can be useful (though TLS covers that mostly). Still, within your database, using constraints (foreign keys, etc.) ensures data consistency. If multiple steps of a workflow happen (like update patient record, send notification, etc.), make sure they either all occur or the system can recover gracefully (transactions or compensating actions) – this is more about reliability, which indirectly ties to compliance (no lost or half-updated records).
Privacy and User Controls: Provide proper audit trails and access reports for users if needed (HIPAA gives patients rights to an accounting of disclosures – meaning you should be able to tell if their data was shared and with whom). Some of this is policy rather than tech, but tech helps generate logs of data access. Additionally, ensure you have a way to delete or archive data if an account is terminated in accordance with regulations (HIPAA doesn’t allow deleting medical records on patient request like GDPR, but you should have a retention and disposal policy when data is no longer needed).
Testing Application Security: As part of DevOps (next section), include security tests in your CI/CD pipeline. If you can, write unit or integration tests for security-related scenarios (e.g., ensure an unauthorized user cannot access a certain API). This can catch regressions in auth logic early.
In essence, Application Security ties together identity management, secure communication, and secure coding to ensure that even at the highest level (where users interact) the best practices are in place. AWS services like Cognito and WAF provide managed solutions for some of these, while others rely on diligent application development. When combined with the secure AWS foundation, features like strong authentication, always-on encryption, and proactive threat prevention (WAF) will harden your application against both common and advanced threats, which is exactly what you need in a healthcare context.
DevOps and Continuous Compliance (CI/CD, Automation, and Governance)
Building a HIPAA-compliant architecture is not a one-time set-and-forget task – it requires continuous maintenance and governance. This is where DevOps processes and automation come in. By integrating security and compliance checks into your development and deployment pipeline, you ensure that every code or infrastructure change is evaluated for its impact on security. Here’s how to approach DevOps in a HIPAA context:
CI/CD Pipeline: Establish a robust Continuous Integration/Continuous Deployment pipeline to automate building, testing, and deploying both your application code and infrastructure code. AWS offers services like CodePipeline, CodeBuild, and CodeDeploy for this purpose, or you can use tools like Jenkins, GitLab CI, etc. The goal is to remove manual deployments, which are error-prone and could inadvertently violate compliance (e.g., someone might skip a step and leave something misconfigured). As one guide noted, manual deploys can introduce human error, whereas a well-configured CI/CD ensures consistency. For infrastructure, if you use CloudFormation or Terraform, include that in the pipeline – e.g., when you push a change to a CloudFormation template in Git, the pipeline runs cfn deploy to apply it, perhaps first in a staging account, runs tests, then promotes to production with an approval step. Include manual approval for production changes if required by your change management process (some organizations need a compliance officer to review changes touching certain resources). AWS CodePipeline supports manual approval steps.
For the application pipeline, integrate security scanning: run static analysis tools (like ESLint, Bandit, etc. depending on language) and dependency vulnerability scanners. AWS CodeGuru (for code analysis) or Amazon Inspector (for scanning images) can be part of this. Failing the build if a critical vulnerability is found will prevent deploying risky code. Also run your test suite – include tests for security (if you have any, like verifying only authorized roles can do certain actions). Ensure your pipeline does not expose secrets – use IAM roles for the pipeline to fetch any needed secrets from Secrets Manager, rather than storing them in plain text.
Infrastructure Testing and Drift Detection: Use tools like Terraform plan (which shows you what changes will happen) or CloudFormation Change Sets to know what a deployment will do. This can be reviewed for any security-impacting change (e.g., opening a new port). After deployment, AWS Config can help detect if anything drifts outside of expected settings (like someone manually changed a security group outside of IaC – Config would flag that). Some organizations enforce that all changes must go through IaC and will treat any drift as non-compliance. You can even use Config rules to detect if a resource was created outside of CloudFormation/Terraform and alert on it.
Automated Compliance Checks: Apart from pipeline tests, use AWS Audit Manager which has a HIPAA assessment framework. This service can continuously gather evidence from your AWS environment to see if you satisfy controls. Audit Manager has pre-built frameworks mapping AWS resources to HIPAA Security Rule criteria, which can be a useful tool to regularly generate reports for auditors. It’s more of a reporting tool, but it helps ensure you’re not missing documentation of compliance.
Environment Separation and Least Privilege for DevOps: Keep your deployment environments separate. Developers should generally not have direct access to production AWS accounts. Instead, they push code and the pipeline (running under its own role) deploys to prod. If direct access is needed (for break-glass situations), it should be tightly controlled and logged (AWS IAM can require MFA and even approve via a ticket). Consider using different AWS accounts for dev/test/prod with AWS Organizations. This not only provides billing separation but also an extra security boundary – someone with dev access can’t mess up prod. Use Service Control Policies (SCPs) in AWS Organizations to enforce baseline restrictions (for example, an SCP could deny the ability to turn off CloudTrail or create certain resources not allowed by policy).
Logging and Monitoring the Pipeline: Treat your CI/CD systems as part of your attack surface. If an attacker compromised your CI/CD, they could inject malicious code. So secure your source control (Git) with MFA and least privilege (only repo collaborators get access). Enable logging for your CI/CD actions – CodePipeline and CodeBuild emit logs to CloudWatch. Monitor those; for instance, alert if a deployment to production happens outside of an approved change window or by an unexpected user. Many breaches come from CI/CD or source control being compromised, so it’s important to protect those as you would production systems.
Backup and Recovery for Code: Keep backups of your code and infrastructure definitions (most companies use distributed version control so it’s inherently backed up across clones, but also maintain an offsite backup or use AWS CodeCommit which stores in S3). Also, ensure you can quickly rollback deployments if a bug or security issue is discovered. Using blue/green or canary deployment strategies (supported by CodeDeploy and other tools) can help deploy changes safely and roll back if issues are detected (which is good for availability and safety).
Documentation and Training: In DevOps, make sure all processes are well-documented – runbooks for deploying, reverting, responding to incidents. HIPAA also has an administrative requirement for training staff. DevOps engineers and developers should be trained on AWS security and your specific policies (like “never put PHI in Jira tickets or Slack”, “how to handle keys”, etc.). Automating reminders or using chatbot integrations (like AWS Chatbot to post to Slack when something needs attention) can keep everyone vigilant.
Continuous Improvement: Finally, adopt a mindset of continuous improvement. Conduct post-mortems after any security incident or even near-miss, and update your processes. AWS Well-Architected Tool has a Security Lens – do those reviews periodically to see if your architecture still follows best practices (AWS often updates their best practices annually). Keep an eye on new AWS services – for example, if AWS releases a new encryption or monitoring feature that could help, plan to integrate it. In the rapidly evolving cloud world, staying current is part of compliance; what was secure in 2018 might need an update by 2025 (for instance, deprecating older TLS or using more automated tooling).
By embedding security and compliance into your DevOps workflows, you ensure that every change is evaluated and that the system doesn’t drift into an insecure state over time. DevOps is sometimes summarized as “automating the guardrails” – you set the standards (guardrails) and let automation enforce them so developers can move quickly within those safe bounds. This approach is perfectly aligned with meeting HIPAA’s ongoing requirements, because compliance isn’t just a one-time checklist, it’s an operational discipline. As one source advises, CI/CD pipelines are highly recommended for HIPAA applications to eliminate the slip-ups that come with manual deployments. Embrace Infrastructure as Code, automated testing, and continuous monitoring in your DevOps culture, and your healthcare application will remain secure and compliant even as it evolves.
Conclusion: Achieving Compliance, Security, and Agility on AWS
Designing a HIPAA-compliant cloud backend on AWS might seem daunting, but as we’ve outlined, AWS provides a rich set of tools and services to address every requirement of the HIPAA Security Rule – from technical safeguards like encryption and access control to operational safeguards like audit logging and disaster recovery. The key is to use these services in concert, following best practices and the principle of least privilege throughout. By leveraging HIPAA-eligible AWS services (ECS, Lambda, RDS, S3, CloudWatch, Cognito, IAM, KMS, and many more) in a well-architected framework, you can build a platform that not only protects patient data but also scales and adapts to your business needs.
In this guide, we discussed an architecture that employs Infrastructure as Code for repeatability, isolated VPC networking for security, scalable compute options for processing, secure storage for sensitive data, asynchronous messaging for decoupling, comprehensive security controls, proactive monitoring and logging, a robust application layer with built-in security, and automated DevOps practices to keep everything in check. This aligns closely with modern 2025 cloud security recommendations – for example, encrypting everything, enforcing MFA, automating compliance checks, and planning for the worst (backups, DR) at every level.
Remember that compliance is an ongoing journey. Regularly review your architecture against AWS’s Well-Architected Framework (Security Pillar) and HIPAA guidelines, as new threats and new AWS features emerge. Maintain documentation of your processes and configurations – this not only helps with audits but also with team turnover and scaling your operations. AWS will continue to expand its compliant service offerings (for instance, recently adding services like Verified Permissions to the HIPAA scope), so stay informed about these updates to continuously improve your stack.
Building a secure, compliant application doesn’t have to slow you down. With the right architecture and automation in place, you can deliver features to your users quickly while keeping their data safe. If you’re starting your journey to HIPAA compliance on AWS or looking to enhance an existing setup, don’t hesitate to leverage AWS resources, partner solutions, or consult experts who specialize in cloud compliance. Ensuring HIPAA compliance can be complex, but you’re not alone – AWS and its community have paved the way with proven patterns and solutions. Take the next step by evaluating your current architecture against the practices discussed here. Implement the safeguards that might be missing, run a compliance tabletop exercise, or reach out for a cloud architecture review. By proactively designing for security and compliance now, you’ll save your organization time, money, and risk in the long run, all while earning the trust of your users that their sensitive health data is well protected.
Let Us Help You Build a Secure, HIPAA-Compliant AWS Architecture
At F3 Software, we help healthcare innovators design, build, and scale cloud-native applications that meet the highest standards of security and compliance. Whether you’re launching a new product or modernizing your existing infrastructure, our team brings the technical expertise and regulatory know-how to guide your journey.
Building a compliant application doesn’t have to slow you down. With the right architecture and automation in place, you can move fast, stay secure, and focus on delivering value to your users.
If you’re starting your path to HIPAA compliance on AWS—or want to strengthen your current cloud environment—F3 Software can help. We work closely with your team to:
- Evaluate your current architecture and identify gaps
- Implement scalable, HIPAA-aligned infrastructure on AWS
- Automate security, backups, and compliance workflows
- Run tabletop exercises and prepare for audits
- Support rapid product delivery without compromising data protection
Let’s build something secure, scalable, and trusted—together.
📩 Contact us today to schedule a cloud architecture review.
Frequently Asked Questions
Related Insights
Related Posts
-
 Case Study: Options Medical Weight Loss
Case Study: Options Medical Weight Loss -
 Case Study: Zoom Tan
Case Study: Zoom Tan -
 Case Study: Evelar Solar
Case Study: Evelar Solar -
 Case Study: FasCat Coaching
Case Study: FasCat Coaching -
 Case Study: verbLIVE
Case Study: verbLIVE -
 Case Study: Persnickety Box
Case Study: Persnickety Box -
 Case Study: Hussle
Case Study: Hussle -
 Testing Software With Agentic AI
Testing Software With Agentic AI -
 Why Experience Unlocks 10x ROI in AI-Driven Software Development
Why Experience Unlocks 10x ROI in AI-Driven Software Development -
 Designing a HIPAA-Compliant Cloud Architecture for Healthcare Apps on AWS
Designing a HIPAA-Compliant Cloud Architecture for Healthcare Apps on AWS